Examining and Enhancing Vehicle Spoofing Detection Capabilities in CAV Applications Using BSM Information
Matthew Barth, Hang Qiu

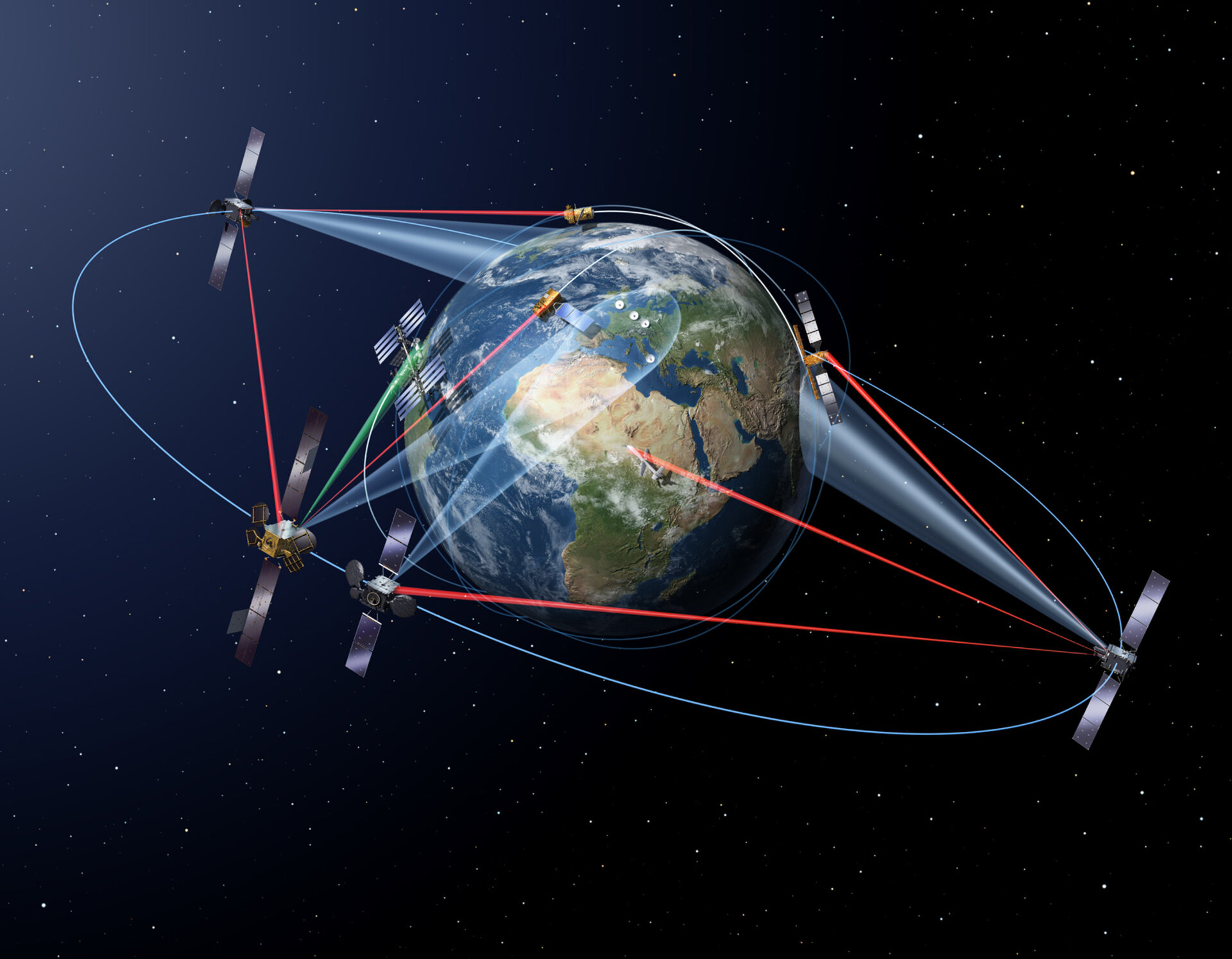
Project Description: In recent years, the frequency of GNSS spoofing attacks has risen significantly. This project aims to enhance vehicle jamming and spoofing detection capabilities in Connected and Autonomous Vehicles (CAV) applications by leveraging information broadcasted by surrounding vehicles and other signals of opportunity in various driving scenarios. The primary focus will be on vehicle-to-vehicle maneuvers, where malicious actors attempt to interfere with cooperative CAV operations. The project will be conducted in a loosely coupled fashion with the CARNATIONS team at Illinois Institute of Technology (IIT). Our collaboration will involve monthly meetings and discussions to exchange ideas, share valuable insights and review progress with the possibility of co-authoring conference papers and journal publications. Moreover, there will be an ongoing collaboration with StarNav to collect real-world spoofing data for the project.
The project will explore a variety of detection opportunities by using data from surrounding vehicles (e.g., BSM data and other shared detection information) and signals of opportunity to identify potential jamming and spoofing attacks and navigation inconsistencies. Key information relevant to the detection system will include vehicle detection and tracking via onboard sensors (e.g., LiDAR, camera) and critical integrity data that is shared between connected vehicles. Additionally, default BSM data such as position, velocity, and heading (along with their uncertainty measures) will be integrated into the detection process.
The project will focus on the detection of two types of spoofing attacks as follows, listed as tasks:
Task 1: The first half of the project will focus on GNSS meaconing detection. Meaconing is a spoofing attack that involves retransmitting GNSS signals with a delay, misleading the receiver into believing it is at a different location or time. This task will consist of two parts:
- Analysis of Spoofing Effects: Investigate and examine how GNSS meaconing affects the behavior and reported data of non-target vehicles in the vicinity, specifically GNSS timing and positioning.
- Identification of Key Detection Information: Determine the critical information needed to detect and mitigate GNSS meaconing to enhance detection accuracy and integrity monitoring. Specifically, the time and direction of arrival of the signal between different vehicles will be explored to identify the key information.
Task 2: the latter half of the project will focus on the worst-case targeted GNSS spoofing attack detection where a bad actor spoofs all satellites to gain control of the target vehicle’s navigation position solution: This task will consist of two parts:
- Analysis of Spoofing Effects: Investigate and examine how GNSS targeted spoofing affects the behavior and reported data of non-target vehicles in the vicinity especially in CAV applications when the spoofing target is the lead vehicle of a platoon.
- Identification of Key Detection Information: Determine the critical information needed to detect and mitigate targeted spoofing attacks, which will be incorporated into the configuration of (possibly) the BSM level 2 custom message or other V2V communication within the platoon to enhance detection accuracy and integrity monitoring.
Throughout the project, the team will incrementally develop and implement a GNSS spoofing detection system through a hardware-in-the-loop (HiL) simulation and real-world data analysis, utilizing surrounding vehicle information and incorporating onboard sensor and BSM data to improve detection capabilities and explore the capability of re-localization of the affected vehicles during spoofing attacks. The simulation will be implemented on an existing HiL testbed for connected and automated vehicles, here at UCR. The real-world spoofing data will be collected in collaboration with StarNav at the PNTAX event.
The tasks are linked in a layered defense strategy by focusing on securing GNSS-based localization in CAVs at different levels of attack sophistication. GNSS meaconing detection serves as a foundational step in understanding and identifying abnormal GNSS signal behavior in non-target vehicles, while targeted spoofing represents a more advanced and deliberate manipulation of GNSS data in critical CAV scenarios, such as spoofing the lead vehicle in a platoon. This approach ensures a comprehensive defense, addressing both lower-level anomalies and more complex attacks.
US DOT Priorities: This research project is focused on addressing the US DOT's priority of enhancing the safety and resilience of the transportation system. We will explore the impact of jamming and spoofing attacks on surrounding vehicles and develop strategies to counteract these threats, utilizing V2X communications. A key aspect of the research is identifying when an attack occurs to boost awareness and reassess the reliability of navigation in such scenarios especially in highway platooning. Ultimately, the goal of the project is to create a resilient set of CAV applications that remains robust in the face of these attacks.
Outputs: In this project, we will:
- Examine jamming and spoofing attack effects on the surrounding non-target vehicles to assess the safety of surrounding vehicles during a spoofing attack during CAV applications. Thus, providing a solution to possible vulnerabilities.
- Propose a BSM level 2 custom message configuration that can help with vehicle spoofing detection by making connected and automated vehicle systems more resilient. Thus, developing a more interconnected system that is resilient to GNSS spoofing attacks.
- Develop a vehicle spoofing detection system that directly contributes to safer roads by detecting navigation and CAV application spoofing attacks which will help in protecting road users.
Outputs/Impacts: The results of this project will address a critical security challenge in the domain of connected and automated vehicles. Moreover, the research will provide a better insight on how spoofing attacks affect nearby non-target vehicles while proposing a detection system that deals with worst case scenario attacks where a bad actor spoofs all navigation signals. Thus, creating a safer and more resilient connected and automated vehicle system.
Final Research Report: Upon completion of the project, we will provide a link to the final report.